...
| Expand | ||
|---|---|---|
| ||
Once the client has been added the external client then needs to visit the following page on Rogo. e.g.
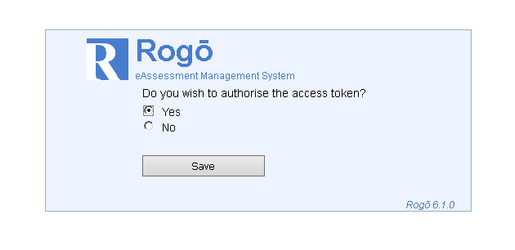
The ‘state’ parameter is intended to preserve some state object set by the client in the Authorization request, and make it available to the client in the response. The main security reason for this is to stop Cross Site Request Forgery (XRSF). An example of this would be a hash of the session cookie or a random value stored in the server linked to the session. Client is required to login as user linked to the client account created in step 1. The logged in user will then be asked to authorise the access rights given in step 1 to the client. An authorisation token will then be generated and returned to the client, for example:
If the client verifies the ‘state’ value returned then it will reject authentication responses that were generated as the result of requests by third party attackers trying to log the user in in the background without the user’s knowledge. |
...
| Expand | |||||
|---|---|---|---|---|---|
| |||||
Client site then uses Authorisation code to request access token, for example the request:
Would get a response like:
The access token can then be used to access web services until expiry. The refresh token can be used to refresh Access token until expiry. From now on you can generate new access and refresh token using your current refresh token (saves you having to login an authorise again):
|
...
| Expand | |||||
|---|---|---|---|---|---|
| |||||
The client can then call the web services with access token in a POST request, for example:
|
...